
Cybercriminals are constantly refining their tactics to breach security systems and steal sensitive information. In this article, we explore how Annexus Technologies can save an organization from a phishing attack, preventing significant financial losses, and provide actionable steps for protecting your institution from similar threats.
Phishing emails can target organizations of any size and type. You might be caught in a mass campaign, where malicious emails are sent indiscriminately to millions of inboxes, or you could be the victim of a more targeted attack. In these targeted campaigns—often called spear phishing—the attacker uses specific information about your employees or company to craft messages that appear highly legitimate and convincing.
Mitigating phishing attacks is not just about protecting your organization; it also contributes to the security of the broader digital landscape. Implementing DMARC (Domain-based Message Authentication, Reporting, and Conformance) can prevent cybercriminals from spoofing your domain, making it significantly more difficult for them to impersonate your company in their attacks. Beyond security, setting up DMARC offers several advantages:
Improved Email Deliverability: Your company's genuine emails are more likely to land in recipients' inboxes, reducing the chances of being flagged as spam.
Enhanced Reputation: Preventing phishing attacks helps your organization avoid being associated with fraud or scams.
Collective Defense: As more companies adopt DMARC, phishing becomes less effective overall, making it harder for cybercriminals to succeed.
What is a Phishing Attack?
Phishing is a type of cyberattack where hackers impersonate trusted entities—such as well-known organizations—to deceive individuals into sharing sensitive data like login credentials, credit card numbers, or other personal information. These attacks often arrive via email, phone, or even text messages, tricking victims into clicking malicious links or downloading malware.
In the case of large organizations, phishing scams can target employees, customers, or even executives. Once inside, cybercriminals can infiltrate systems and gain access to sensitive data, leading to devastating consequences, such as siphoning off funds, stealing identities, or compromising entire networks.
Phishing attacks have become increasingly efficient. In 2023, 96% of targeted organizations were negatively impacted by phishing attacks, up from 86% the previous year. Moreover, 58% of organizations experienced account takeovers, with 79% of those resulting from credentials harvested through phishing attacks. These statistics highlight how crucial it is for organizations to remain vigilant and adopt robust security measures to protect against these sophisticated threats.
Types of Phishing Attacks
If you’ve been phished, chances are the attack was delivered in one of these ways:
Smishing: Bad actors send users an SMS message containing a link to a phishing site, often with the intent to steal user credentials.
Whishing: Similar to smishing, bad actors send malicious messages via WhatsApp.
Email Phishing: Phishing attempts can target personal or corporate emails, appearing to be from a familiar organization or website. These emails may ask users to log in to software they use, ultimately directing them to a malicious but legitimate-looking site.
Vishing: Voice phishing may involve spoofed numbers that appear to be from legitimate institutions. These attacks often use a text-to-speech program or a real voice and are used to obtain financial information from victims.
Spear Phishing: These attacks are sent to specific targets or groups, such as members of the IT department, through email, text, or other means. Attackers may impersonate a known individual, asking for assistance or personal information.
Whaling: This type targets high-profile executives, often impersonating other executives to appear legitimate, eventually sending victims to a spoofed site to harvest credentials or authorize payments on fake invoices.
Social Media: Bad actors increasingly use social media to reach their victims, often employing spoofed identities, such as an administrator for the service, to gather personal information.
How Actifile Helps Prevent Data Exfiltration
In today’s digital landscape, data exfiltration poses a significant threat to organizations. Actifile, a powerful data security and privacy solution, empowers Managed Service Providers (MSPs) to combat this growing challenge effectively. Here’s how Actifile can bolster your institution's defenses:
Real-time Data Monitoring: Actifile provides comprehensive visibility into data flows across your network, enabling immediate detection of unusual access patterns and potential exfiltration activities. This proactive approach allows organizations to act swiftly before any significant damage occurs.
Automated Risk Assessment: Utilizing advanced AI-powered tools, Actifile continuously assesses potential risks associated with user behavior. By flagging suspicious activities, such as unauthorized login attempts or data transfers, it equips teams with the information needed to respond promptly.
Data Loss Prevention (DLP): Actifile implements robust DLP strategies, ensuring that sensitive data is identified, monitored, and protected against unauthorized transfers. By restricting access to critical information and tracking data movement, organizations can significantly mitigate the risk of data loss.
Incident Response Support: In the unfortunate event of a data breach, Actifile facilitates an effective incident response. Its tools help identify the source and scope of the breach, allowing organizations to contain the threat and recover lost data swiftly.
Comprehensive Training Resources: Actifile not only protects data but also empowers organizations through educational resources. By promoting cybersecurity best practices and employee awareness, it helps create a culture of vigilance against potential threats.
With Actifile, institutions can strengthen their security posture against data exfiltration, protecting sensitive information from both insider threats and external cybercriminals. As cyberattacks become increasingly sophisticated, investing in advanced security solutions like Actifile is essential for safeguarding your organization’s critical data.
5 Ways to Protect Your Institution from Phishing Attacks
Employee Training and Awareness: One of the most effective defenses against phishing attacks is educating employees about the risks. Regular cybersecurity training can empower staff to recognize suspicious emails, links, and attachments, thereby reducing the likelihood of falling victim to such scams. Simulations of phishing attempts can further enhance their skills and awareness.
Implement Multi-Factor Authentication (MFA): MFA adds an extra layer of security by requiring multiple forms of verification before granting access to sensitive systems. Even if hackers manage to obtain login credentials, MFA serves as a robust barrier, significantly lowering the chances of unauthorized access.
Use Data Encryption: Ensure that all sensitive information is encrypted both in transit and at rest. This measure makes it exceedingly difficult for hackers to interpret any data they manage to intercept, protecting your organization from potential breaches.
Deploy Anti-Phishing Tools: Tools like Actifile provide comprehensive monitoring and detection capabilities, identifying phishing attempts before they can infiltrate your systems. Actifile offers features such as real-time monitoring, automated data loss prevention, and advanced file encryption, allowing organizations to swiftly neutralize threats. With Actifile's proactive approach, institutions can significantly enhance their defenses against phishing.
Regular Security Audits: Conduct frequent security assessments and audits to identify vulnerabilities within your systems. Phishing tactics evolve rapidly, making it essential to stay up-to-date with the latest security patches and threat detection systems. Regular audits can help you understand your security posture and make informed decisions to strengthen it.
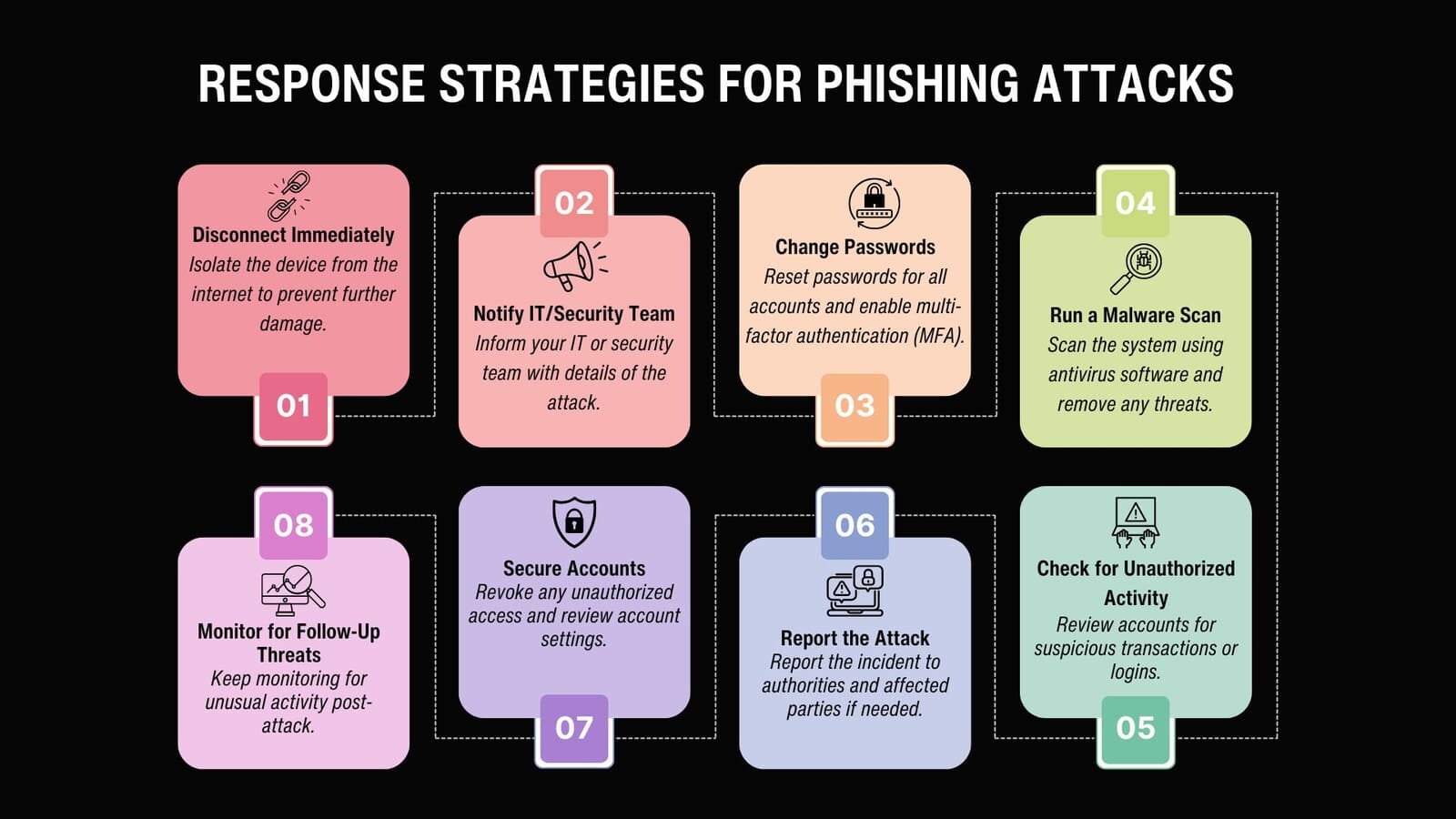
Phishing attacks are a growing threat to organizations, but with the right tools and strategies in place, you can protect your institution from potentially devastating breaches. At Annexus Technologies, we specialize in preventing cybersecurity threats, safeguarding sensitive data, and providing tailored solutions to our clients.
If your institution is looking for expert guidance on preventing phishing attacks, contact Annexus Technologies today to book a consultation. Our team is ready to help you strengthen your defenses and ensure the safety of your critical information.

