Wireless Security Assessment in Focus

As businesses in Jamaica and around the world embrace digital transformation, the demand for reliable and high-speed Wireless Internet Connectivity continues to soar. In November 2023, Jamaica witnessed significant progress in mobile and fixed broadband Internet speeds, with the median mobile Internet download speed reaching 29.7 Mbps and the median fixed broadband download speed hitting 60.78 Mbps. Additionally, at the beginning of the year, approximately 82 percent of people in the Caribbean country were online, highlighting the growing reliance on digital technologies for both personal and professional use. However, amidst this digital evolution, businesses must also contend with the ever-present threat of cybersecurity breaches and vulnerabilities. With cybercriminals becoming increasingly sophisticated in their tactics, protecting your wireless infrastructure has never been more crucial. At Annexus Technologies, we recognize the paramount importance of safeguarding your wireless network against potential security risks. That's why we offer a comprehensive Wireless Network Security Assessment tailored to your organization's unique needs and security requirements.
Why Conduct a Wireless Security Assessment?
In today's interconnected world, businesses rely heavily on wireless networks to facilitate communication, collaboration, and data access. However, the convenience of wireless connectivity also presents vulnerabilities that cybercriminals can exploit to gain unauthorized access to sensitive information. A Wireless Security Assessment is essential for identifying potential risks and vulnerabilities in your wireless network infrastructure, allowing you to proactively address security gaps and mitigate potential threats.
Our Approach: Ensuring Comprehensive Coverage
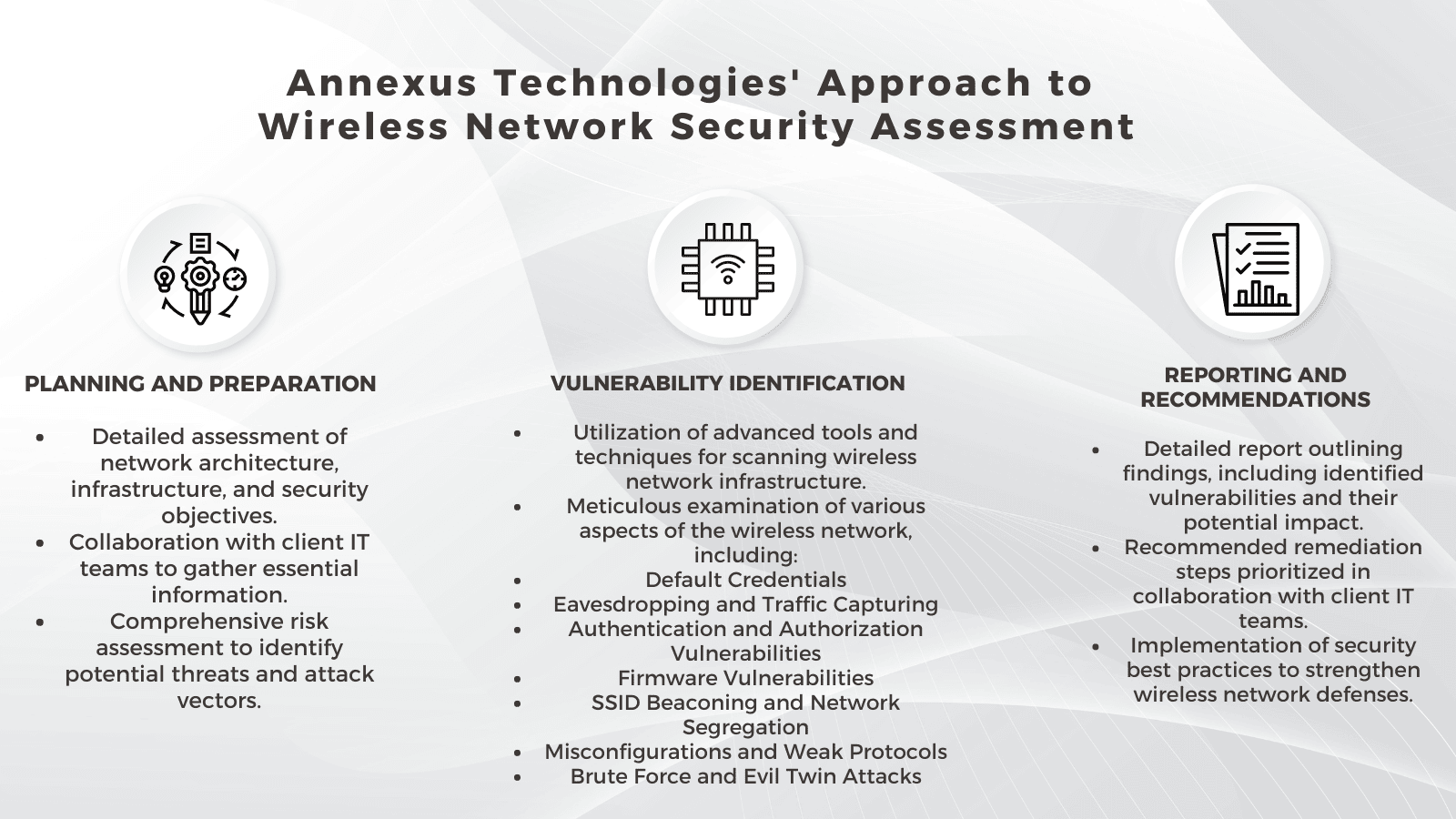
At Annexus Technologies, we take a systematic and holistic approach to Wireless Network Security Assessment, ensuring thorough coverage and accurate identification of vulnerabilities. Our approach consists of the following key components:
Planning and Preparation
Before commencing the assessment, our team conducts a detailed planning phase to understand your organization's network architecture, infrastructure, and security objectives. We work closely with your IT team to gather essential information about your wireless network setup, including the types of devices, access points, and security protocols in use. Additionally, we conduct a comprehensive risk assessment to identify potential threats and attack vectors specific to your environment.
Vulnerability Identification
Once the planning phase is complete, we proceed to the vulnerability identification stage, where we leverage advanced tools and techniques to scan your wireless network infrastructure for potential vulnerabilities. Our team meticulously examines various aspects of your wireless network, including:
Default Credentials: Identifying and addressing default login credentials that could be exploited by malicious actors to gain unauthorized access.
Eavesdropping and Traffic Capturing: Detecting potential threats from unauthorized access points and monitoring network traffic for signs of malicious activity.
Authentication and Authorization Vulnerabilities: Evaluating the effectiveness of authentication mechanisms and access controls to prevent unauthorized access.
Firmware Vulnerabilities: Assessing the security posture of wireless access points and identifying potential firmware vulnerabilities that could be exploited by attackers.
SSID Beaconing and Network Segregation: Ensuring proper configuration of SSIDs and detecting hidden or rogue wireless networks that could pose security risks.
Misconfigurations and Weak Protocols: Identifying configuration errors and vulnerabilities in wireless network protocols that could be exploited by attackers.
Brute Force and Evil Twin Attacks: Assessing susceptibility to brute force attacks and rogue access point exploitation, and implementing measures to mitigate these risks.
Reporting and Recommendations
Following the vulnerability identification stage, we provide you with a detailed report outlining our findings, including identified vulnerabilities, their potential impact, and recommended remediation steps. Our expert consultants work closely with your IT team to prioritize remediation efforts and implement security best practices to strengthen your wireless network defenses.
Key Assessment Areas
Default Credentials: Default login credentials are often overlooked but can pose a significant security risk if not changed. We identify and address default credentials to prevent unauthorized access to your wireless network infrastructure.
Eavesdropping and Traffic Capturing: Unauthorized access points and eavesdropping attacks can compromise the confidentiality of your network traffic. We monitor network traffic for signs of eavesdropping and implement measures to secure your wireless communications.
Authentication and Authorization Vulnerabilities: Weak authentication mechanisms and inadequate access controls can lead to unauthorized access to your wireless network. We evaluate the effectiveness of your authentication protocols and access controls to prevent unauthorized access and strengthen security.
Firmware Vulnerabilities: Outdated firmware on wireless access points can contain vulnerabilities that could be exploited by attackers. We assess the security posture of your access points and identify and remediate firmware vulnerabilities to reduce the risk of exploitation.
SSID Beaconing and Network Segregation: Proper SSID configuration and network segregation are essential for preventing unauthorized access and maintaining network security. We ensure that your SSIDs are properly configured and detect any hidden or rogue wireless networks that could pose security risks.
Misconfigurations and Weak Protocols: Configuration errors and weak protocols can create security vulnerabilities that could be exploited by attackers. We identify and remediate misconfigurations and weaknesses in wireless network protocols to enhance security.
Brute Force and Evil Twin Attacks: Brute force attacks and evil twin attacks can compromise the integrity and confidentiality of your wireless network. We assess susceptibility to these attacks and implement measures to mitigate these risks, such as implementing stronger authentication mechanisms and monitoring for rogue access points.
Benefits of Wireless Network Security Assessment
A Wireless Network Security Assessment empowers businesses to fortify their wireless infrastructure, enhancing overall security posture. By proactively identifying and addressing vulnerabilities, organizations can mitigate the risk of cyber threats and protect sensitive data. This comprehensive assessment ensures compliance with industry regulations, bolstering trust and safeguarding the organization's reputation.
By partnering with Annexus Technologies for a Wireless Network Security Assessment, you can:
Enhance the security posture of your wireless network infrastructure.
Identify and remediate vulnerabilities before they are exploited by malicious actors.
Ensure compliance with industry regulations and standards.
Safeguard sensitive data and protect your organization's reputation.
As businesses in Jamaica and around the world embrace digital transformation, the demand for reliable and high-speed wireless internet connectivity continues to soar. In November 2023, Jamaica witnessed significant progress in mobile and fixed broadband internet speeds, with the median mobile internet download speed reaching 29.7 Mbps and the median fixed broadband download speed hitting 60.78 Mbps. Additionally, at the beginning of the year, approximately 82 percent of people in the Caribbean country were online, highlighting the growing reliance on digital technologies for both personal and professional use.
However, amidst this digital evolution, businesses must also contend with the ever-present threat of cybersecurity breaches and vulnerabilities. With cybercriminals becoming increasingly sophisticated in their tactics, protecting your wireless infrastructure has never been more crucial. The consequences of a security breach can be devastating, resulting in data loss, financial losses, and damage to your organization's reputation.
At Annexus Technologies, we recognize the paramount importance of safeguarding your wireless network against potential security risks. Our Wireless Network Security Assessment is designed to provide you with a comprehensive understanding of your network's security posture and identify potential vulnerabilities that could be exploited by malicious actors. By partnering with us, you can take proactive steps to strengthen your network defenses and protect your organization's valuable assets.
Our approach to Wireless Network Security Assessment is meticulous and thorough, ensuring that no stone is left unturned in identifying and addressing potential security risks. From planning and preparation to vulnerability identification and reporting, we work closely with your organization to develop tailored recommendations that align with your unique security requirements.
By investing in a Wireless Network Security Assessment with Annexus Technologies, you can gain peace of mind knowing that your wireless infrastructure is fortified against cyber threats. Don't wait until it's too late. Take proactive steps to protect your organization's digital assets today.
Book a free consultation with Annexus Technologies to learn more about how we can help safeguard your wireless network. Whether you're based in Canada, the Caribbean, or the USA, our team of experts is here to support you on your journey to a more secure digital future.

