Exploring the Importance, Benefits, and Implementation Strategies of Network Segmentation for Enhanced Data Security

If you keep up with cybersecurity news, you are probably aware that the cost and occurrence of data breaches continue to rise. Organizations are under continual attack, and the transition to remote labor is intensifying the issue.
Exploring Network Segmentation
In this post, we'll delve into network segmentation, covering its significance, advantages, and strategies for implementation.
What is Network Segmentation?
Network segmentation is an architectural technique for dividing a network into many parts or subnets, each of which functions as its own separate network. This allows network managers to use granular policies to govern traffic flow between subnets. Segmentation is used by businesses to increase monitoring, performance, pinpoint technical faults, and, most critically, improve security.
Network segmentation successfully prevents a single point of failure and makes it impossible for unauthorized users to jeopardize the whole network by isolating (or segmenting) the network into discrete contained pieces.
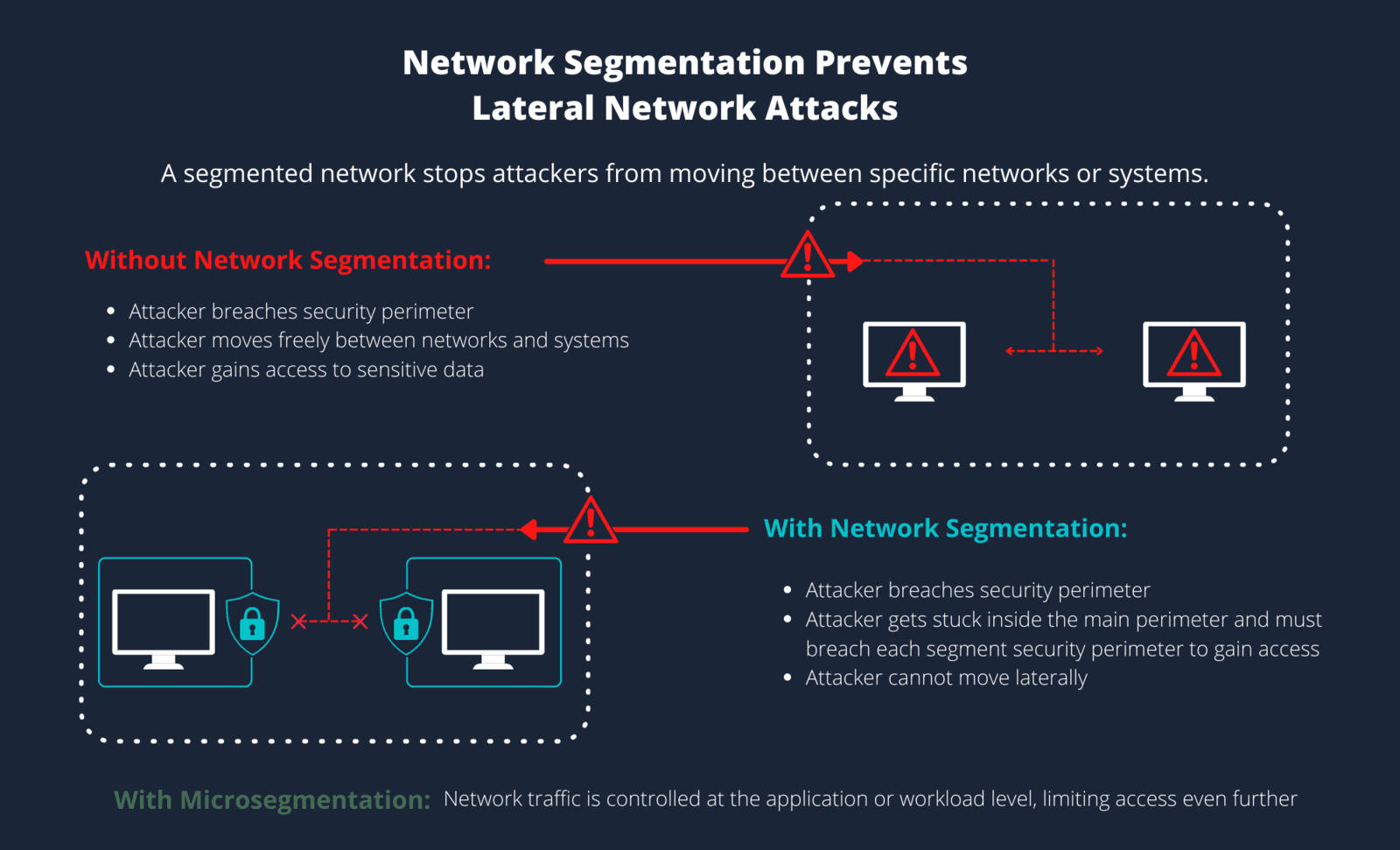
Advantages of Network Segmentation
- Enhanced Monitoring: Allows for the logging of events, the monitoring of approved and forbidden internal connections, and the detection of suspect activity.
- Enhanced Performance: Local traffic is reduced when there are fewer hosts per subnet. Broadcast traffic can be restricted to a single subnet.
- Enhanced Security: To limit and/or prevent access between network parts, network traffic can be separated and/or filtered.
- Improved Containment: When a network problem occurs, its impact is restricted to the local subnet.
- Improved Access Control: Allow users to access just particular network resources.
Meeting Zero Trust and Compliance Requirements
You have possibly heard of zero trust, a prominent network security concept that solves the cybersecurity challenges that most businesses face today. Nothing, even users or programs currently inside the network perimeter, should be trusted by default in a zero trust environment.
While network segmentation is a concept and a method, it symbolizes a larger movement in cybersecurity philosophy toward the zero-trust paradigm. By segmenting network routes, you're adopting the "trust no one" mentality.
Planning and Execution Strategies
To prevent both over and under segmentation, it's critical to build your strategy around clear rules that you can follow to get the best outcomes. Some key strategies include:
- Clear Vision: Assessing the existing state of the company's security and creating a picture of what needs to be done to enhance it.
- Revision of Current Security Framework: Auditing the existing network, seeing what security features are already in place, and emphasizing what's working and what needs to be enhanced.
- Create an Action Roadmap: Breaking down the implementation plan into smaller chunks to spot any areas where you can enhance or make a minor strategy modification along the road.
Ready to enhance your network security through segmentation? Contact us today to learn how our experts can help you implement a robust network segmentation strategy tailored to your business needs.

