Strengthening Email Security with Domain-based Message Authentication, Reporting, and Conformance (DMARC)
Email remains the backbone of modern business communication. It powers everything from contract negotiations and payment approvals to customer engagement and internal collaboration. Yet, this very reliance has made email the most exploited attack vector in cybersecurity. According to the FBI’s 2024 Internet Crime Report, Business Email Compromise (BEC) alone caused over $2.9 billion in reported losses worldwide, with phishing attacks accounting for nearly 70% of all breaches.
The danger lies in simplicity: attackers do not need to hack into your systems—they only need to convince someone that a malicious message came from you. Spoofed domains, fraudulent invoices, and fake executive requests are enough to cause financial and reputational damage within minutes.
This is where DMARC (Domain-based Message Authentication, Reporting, and Conformance) becomes essential. Acting as a passport control system for your email domain, DMARC validates that only authorized senders can use your company’s identity. Unauthenticated messages are blocked or flagged before they ever reach an inbox, protecting your brand, your employees, and your customers from costly deception.
What Is DMARC?
At its core, DMARC (Domain-based Message Authentication, Reporting, and Conformance) is an advanced email authentication protocol designed to stop attackers from sending emails that appear to come from your organization. It builds on two widely adopted standards:
SPF (Sender Policy Framework): Think of SPF as a guest list for your domain. It specifies which servers are allowed to send emails on your behalf. If a server isn’t on the list, its messages fail the check.
DKIM (DomainKeys Identified Mail): DKIM works like a digital wax seal. Each email carries a cryptographic signature that verifies the message has not been altered in transit and truly originates from your domain.
DMARC: Acting as the gatekeeper, DMARC reviews the results of both SPF and DKIM. If the message fails these checks, DMARC enforces your policy—whether that is allowing the message through, sending it to spam, or rejecting it outright.
Beyond blocking impersonation, DMARC delivers another critical advantage: visibility. Through detailed reports, organizations can see who is sending email on their behalf, detect unauthorized usage of their domains, and strengthen their overall email ecosystem. This reporting function is often overlooked, but it is one of the most valuable tools for security teams trying to understand and defend against evolving threats.
In simple terms: SPF verifies the sender, DKIM secures the content, and DMARC ensures compliance while giving you insights into domain activity. Together, they form a powerful shield against email phishing, domain spoofing, and fraud.
Why Your Business Needs DMARC
Prevent Email Spoofing & PhishingPhishing remains the most common cyber threat, with 3.4 billion fake emails sent daily, according to the FBI and Proofpoint research. Attackers frequently impersonate executives or vendors to trick employees into wiring funds or sharing sensitive data. With DMARC in place, these fraudulent emails are rejected before they ever reach an inbox.
Protect Your Brand ReputationYour domain is more than just a technical asset—it is the digital face of your business. A single spoofed campaign can erode customer trust overnight. Studies show that 91% of consumers will not do business with a company after a phishing attack compromises their data. By implementing DMARC, you safeguard your brand identity and demonstrate to partners and clients that security is a priority.
Improve Email DeliverabilityMajor providers like Google and Microsoft favor authenticated domains. Organizations using DMARC correctly often see improved inbox placement rates of up to 10–15%, ensuring that marketing campaigns, customer updates, and critical communications are delivered instead of being flagged as spam.
Gain Full VisibilityDMARC reporting functions like CCTV for your email traffic. You gain detailed insight into who is sending on your behalf—whether it is internal systems, trusted third-party services (like CRMs or marketing tools), or malicious actors. This visibility empowers IT teams to close security gaps before they are exploited.
How DMARC Works
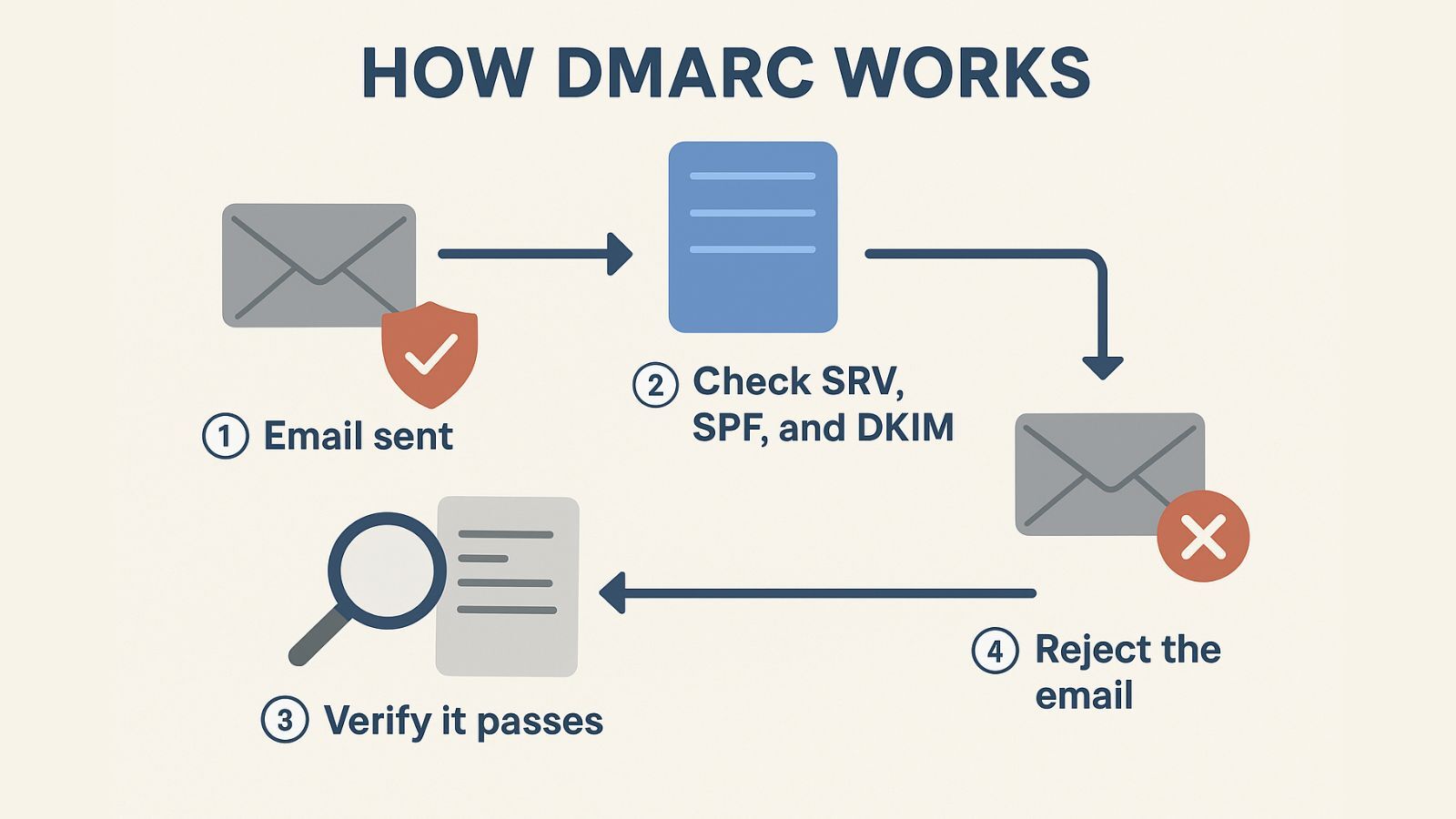
Implementing DMARC begins with publishing a DMARC record in your DNS—the internet’s “address book.” This record acts as a set of global instructions that tells receiving mail servers how to handle messages sent from your domain.
When an email is sent, three checks take place:
SPF verification confirms the sending server is on your authorized list.
DKIM verification ensures the message has not been tampered with.
DMARC alignment compares both results against your domain policy to decide whether the email should be delivered, quarantined, or rejected.
This layered process creates a defense-in-depth strategy that makes domain impersonation significantly harder for attackers.
Understanding DMARC Records
A DMARC record might look complex at first glance, but it is essentially a set of instructions written as a short line of text in DNS. Example:
v=DMARC1; p="reject;" rua="mailto:reports@company.com;" ruf="mailto:forensics@company.com;" pct="100
Breakdown:
v=DMARC1 → Protocol version.
p=reject → Policy: block emails that fail authentication.
rua= → Address for receiving daily summary (aggregate) reports.
ruf= → Address for detailed forensic reports.
pct=100 → Enforce the policy on 100% of messages.
Plain language: “Check all my emails, block the fake ones, and send me reports on activity.”
DMARC Policies Explained
DMARC policies allow organizations to gradually increase security without disrupting legitimate email:
p=none (Monitor Mode): Emails are delivered normally, but reports are generated. Best for initial setup.
p=quarantine (Warning Mode): Suspicious messages are sent to recipients’ spam/junk folders. Useful for testing enforcement.
p=reject (Strict Mode): Unauthorized emails are blocked completely. This is the end goal for mature organizations.
According to Gartner, over 70% of companies adopting DMARC begin with “none” and take 6–12 months before moving to “reject.” This phased approach helps identify legitimate third-party senders that must be authorized before full enforcement.
DMARC Reports: Your Visibility Tool
One of DMARC’s most powerful features is the reporting system, which turns invisible email traffic into actionable intelligence:
Aggregate Reports: High-level daily summaries showing how many emails passed, failed, or were suspicious.
Forensic Reports: Detailed records of individual failed messages, including headers, IPs, and sometimes full email samples.
With these reports, IT teams can fine-tune configurations, detect abuse early, and continuously strengthen their domain’s security posture. Over time, this creates a real-time feedback loop, ensuring your defenses evolve alongside attackers.
Common Misconceptions About DMARC
Best Practices for Implementing DMARC
- Start with p=none to monitor safelyBegin in Monitor Mode to map all legitimate senders without impacting email delivery. This approach lets you understand your email ecosystem and catch any misconfigurations early.
- Identify all legitimate sendersInclude internal systems and third-party services like CRMs, marketing platforms, payroll systems, or cloud services. Missing any authorized sender can result in legitimate emails being blocked once stricter policies are applied.
- Leverage DMARC analysis toolsDMARC reports are delivered in XML format, which can be complex to interpret manually. Use specialized tools to simplify the data, spot anomalies, and visualize trends in email traffic. This helps prioritize actions and detect potential threats quickly.
- Gradually move to stricter policiesTransition from p=none to p=quarantine, then eventually to p=reject. A phased approach reduces the risk of accidental delivery failures and ensures full protection without disrupting business communications.
- Review reports regularly and adjust policiesContinuous monitoring is key. Analyze aggregate and forensic reports to identify new senders, misconfigurations, or suspicious activity. Adjust policies and authorized sender lists as needed to maintain a secure and reliable email system.
Pro Tip: Organizations that follow this structured approach often reach full enforcement in 6–12 months with minimal disruption and maximum protection against email fraud.
Email may be one of the oldest digital communication tools, but it remains the most heavily targeted by cybercriminals. Phishing, spoofing, and business email compromise continue to cause billions in losses each year, and traditional defenses alone are no longer enough. DMARC provides a proven, standards-based way to protect your domain, build trust with customers, and gain critical visibility into how your email is being used.
Adopting DMARC is not just about compliance or security—it is about safeguarding the lifeline of your business communication. From preventing fraud to improving deliverability, the benefits extend across every layer of your organization.
At Annexus Technologies, we help businesses implement and manage DMARC the right way—from setup and monitoring to fine-tuning policies for maximum protection. With our expertise, you can secure your communications, protect your reputation, and stay one step ahead of attackers.


