
Is your organization doing enough to secure its network? As businesses grow and digital threats become more complex, network security must evolve. One of the most effective strategies to strengthen cybersecurity is network segmentation—but what exactly does that mean?
Network segmentation is the practice of dividing a computer network into smaller, isolated segments or zones. This division allows businesses to control and monitor traffic flow, applying security policies that prevent unauthorized access to sensitive data and systems. By segmenting your network, you essentially create layers of protection, making it harder for attackers to move through your system once they have breached one segment.
The Power of Network Segmentation in Cybersecurity
In a 2023 report by Cisco, 73% of security professionals said that network segmentation was a critical element in preventing lateral movement during a cyberattack. This means that if one part of your network is compromised, the rest of your business operations can still remain secure. But it is not just about defense—it is about visibility, control, and performance.
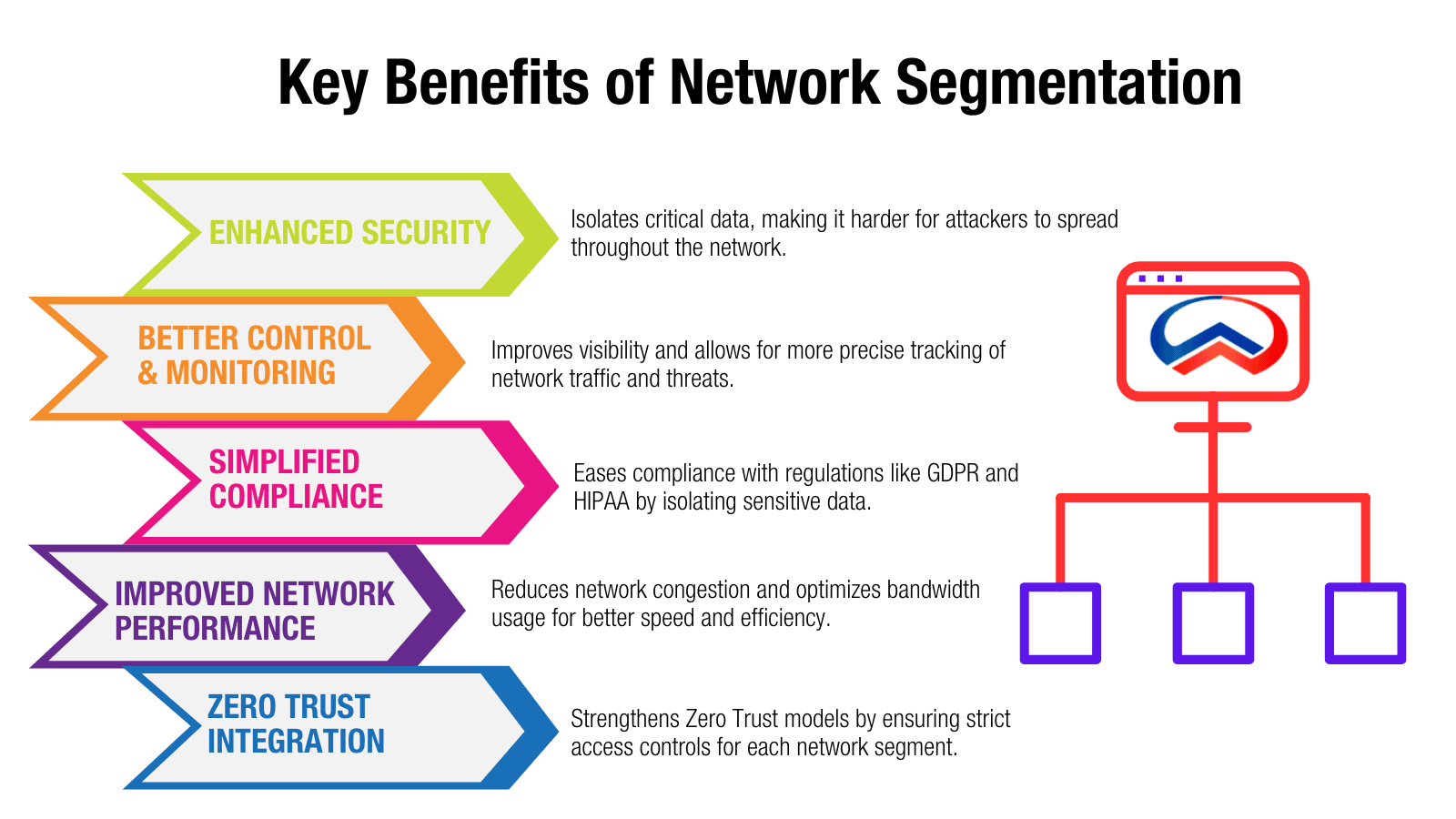
Network segmentation gives businesses the ability to isolate critical infrastructure, enforce stricter access controls, and improve both security and network performance. It also enhances threat detection, as segmented networks allow for more detailed monitoring of traffic, helping identify suspicious activities early on. By controlling access based on specific needs, you can minimize the potential for human error or insider threats.
Moreover, segmentation can simplify compliance with industry regulations, as it is easier to control and audit access to sensitive data within isolated segments. With the growing complexity of IT environments, segmentation allows businesses to scale their security measures more effectively, adapting to new technologies or increased risk levels.
1. Reduce the Impact of Cyberattacks with Layered Security
Cyberattacks are inevitable, but their impact does not have to be catastrophic. In 2023, IBM reported that the average cost of a data breach reached $4.45 million, with lateral movement within a network being a significant contributor to the damage. Attackers who gain initial access to a network often exploit the ability to move freely across systems, which can lead to widespread compromise of sensitive data, intellectual property, and business operations. Network segmentation addresses this issue by reducing the attack surface and making it much harder for attackers to spread.
By dividing your network into isolated segments, you create barriers that limit the movement of cybercriminals within the system. Even if one segment is compromised, attackers are unable to easily traverse to other sections of the network, which helps to contain the breach and minimize overall damage. This segmentation also improves your ability to detect suspicious activity more quickly, as anomalies in one segment are easier to identify compared to a larger, unsegmented network.
Tip: Start by segmenting your most valuable assets, such as financial data or customer information, into isolated sections. By doing so, you reduce the risk of widespread damage in the event of a breach.
2. Achieve Greater Visibility and Control Over Your Network
The more segments you have, the better the visibility you gain into internal traffic. A segmented network provides a granular view of traffic flow, allowing security teams to identify and monitor interactions between distinct parts of the network. By isolating key assets and services, you create clear boundaries that make it easier to track traffic patterns, detect potential threats, and identify abnormal behaviors. This increased visibility is crucial for catching issues early, as suspicious activity becomes more apparent in segmented environments where it stands out against the norm.
In fact, organizations that have implemented network segmentation have reported a 40% improvement in their ability to detect and respond to security incidents more rapidly. The ability to quickly pinpoint the source and extent of an attack is critical to minimizing damage and reducing recovery times. Segmentation also allows teams to apply tailored security measures for each segment, which strengthens defenses and ensures that sensitive areas receive extra protection.
Tip: Use network monitoring tools to track interactions between segments and deploy intrusion detection systems (IDS) on key boundaries. This proactive monitoring ensures you catch suspicious activity before it escalates.
3. Strengthen Zero Trust Policies with Granular Access Control
Trusting any user or device without verification is risky in today’s security environment. The Zero Trust model operates under the assumption that threats can originate both inside and outside the network, meaning that no user or device should be trusted by default. It emphasizes continuous verification—ensuring that access to systems and data is only granted when users and devices meet specific security requirements. This approach challenges the traditional security model where the network perimeter was considered the primary point of defense, recognizing that modern cyber threats often bypass perimeter defenses.
Network segmentation plays a critical role in Zero Trust by enabling granular access control based on roles, permissions, and specific security policies. It allows organizations to create isolated zones within the network, enforcing strict boundaries around sensitive data and critical systems. By doing so, businesses can tightly control who can access what and under which conditions, significantly reducing the risk of unauthorized access and lateral movement within the network.
Tip: Implement microsegmentation for even tighter control. Microsegmentation isolates specific workloads and applications, offering more precise control over access and reducing the risk of insider threats. According to Gartner, companies that use microsegmentation reduce the potential impact of an attack by 30%.
4. Improve Network Performance and Efficiency
Network congestion is a common challenge in larger, unsegmented networks. When all devices share the same network space, traffic can quickly become bottlenecked, leading to slower speeds and inefficient bandwidth usage. By dividing the network into smaller, more manageable segments, organizations can ensure that traffic is routed more efficiently, avoiding congestion and improving both speed and bandwidth allocation. Each segment operates more independently, reducing the likelihood of slowdowns caused by high traffic volumes in one area of the network.
In fact, network segmentation can reduce latency and improve overall network performance by up to 20% in certain environments. With less data traveling across a single network, resources are better distributed, leading to faster response times and more reliable performance. Segmentation also allows for tailored optimization in each segment, addressing specific performance needs based on the criticality of the systems or applications within them.
Tip: Use Quality of Service (QoS) policies to prioritize mission-critical applications in segmented zones. This ensures your key systems always have the resources they need, especially during periods of heavy traffic, preventing network slowdowns from affecting vital business operations.
5. Simplify Compliance and Regulatory Requirements
For organizations handling sensitive data, network segmentation plays a key role in streamlining compliance with industry regulations such as GDPR and HIPAA. These regulations require strict controls on how data is accessed, stored, and transferred. By isolating sensitive data within dedicated network segments, businesses can reduce the scope of compliance audits, making it easier to demonstrate adherence to regulatory standards. Segmenting protected data minimizes the risk of exposing it to unauthorized access or data breaches, as sensitive information is contained within secure boundaries.
Moreover, segmentation simplifies the enforcement of controls such as encryption, access logs, and multi-factor authentication—key components of many compliance frameworks. Organizations can focus their efforts on protecting a smaller set of critical systems, reducing the administrative burden of compliance and mitigating the risk of penalties from non-compliance.
Tip: Create dedicated segments for sensitive data, ensuring that only authorized users have access. This reduces your risk of non-compliance during audits, as only the relevant segments will be scrutinized, making it easier to demonstrate your organization’s compliance with regulatory requirements.
6. Defend Against Insider Threats
Network segmentation is a key strategy for reducing the risks posed by insider threats, whether accidental or malicious. By limiting access to sensitive systems, organizations can contain the impact of unauthorized actions and reduce the likelihood of data breaches. Segmentation creates clear boundaries within the network, enabling faster detection and isolation of suspicious activity.
Additionally, segmentation enhances the enforcement of security controls such as access restrictions, real-time monitoring, and role-based permissions. With smaller, isolated segments, businesses can better protect critical assets while maintaining operational efficiency.
Tip: Design segments around role-based access needs, restricting users to only the data and systems required for their tasks. This limits exposure to sensitive information and minimizes insider risks.
Future-Proof Your Security with Network Segmentation
Network segmentation is no longer optional—it is a crucial element in protecting your business from evolving cyber threats. By isolating sensitive data and controlling access, businesses can minimize unauthorized access and reduce the attack surface, making it harder for cybercriminals to move laterally through the network. This helps prevent widespread damage in the event of a breach.
Segmentation also enhances visibility by enabling better monitoring of traffic between network boundaries, improving threat detection and response times. Furthermore, it boosts network performance by managing traffic more efficiently, ensuring that critical systems are prioritized and thus reducing congestion.
As businesses grow and adopt new technologies, network segmentation offers the flexibility to scale with evolving security needs. It also forms a foundational layer for advanced security models like Zero Trust, where every access request is verified.
In short, network segmentation strengthens your security posture, improves performance, and future-proofs your organization against new threats and challenges.
At Annexus Technologies, we specialize in implementing robust network segmentation solutions tailored to your business needs. Ready to enhance your network security and performance? Contact us today to discuss how we can help protect your business from evolving cyber threats.

