An organization’s attack surface is the total sum of all devices, access points, and IT assets that cybercriminals may target to gain access. This includes endpoint devices, user accounts, software vulnerabilities, and connected hardware.
As businesses expand their digital footprint, their attack surface grows—creating more opportunities for cyber threats. The consequences of failing to secure this ever-expanding landscape can be severe, as seen in the increasing number of companies suffering breaches that expose sensitive customer data and corporate information.
What is Attack Surface Monitoring?
Attack surface monitoring is the continuous process of assessing and managing the size, structure, and security of an organization’s attack surface. It helps identify vulnerabilities, detect potential threats, and mitigate risks such as ransomware, credential theft, and social engineering attacks before they can be exploited.
How Can You Secure What You Don’t Know You Have?
In cybersecurity, visibility is crucial. Yet, many organizations still face significant gaps in their understanding of their own attack surface. Gartner predicts that 30% of successful cyberattacks this year will target shadow IT—systems, devices, or applications that IT teams are unaware of but are in active use within the organization.
It is no secret that managing an attack surface has become increasingly challenging. According to the latest ESG report, Attack Surface and Vulnerability Management Assessment, two-thirds of CISOs report that attack surface management is now more difficult than it was just two years ago. As organizations expand their digital footprints and adopt new technologies, it is clear that attack surface management needs to be a top priority.
But with the complexity growing, how can businesses stay ahead of the curve? To help, we have identified four common mistakes organizations make in managing their attack surface and how you can avoid them to strengthen your cybersecurity posture.
Identifying and Securing Your Attack Surface: 12 Critical Checks
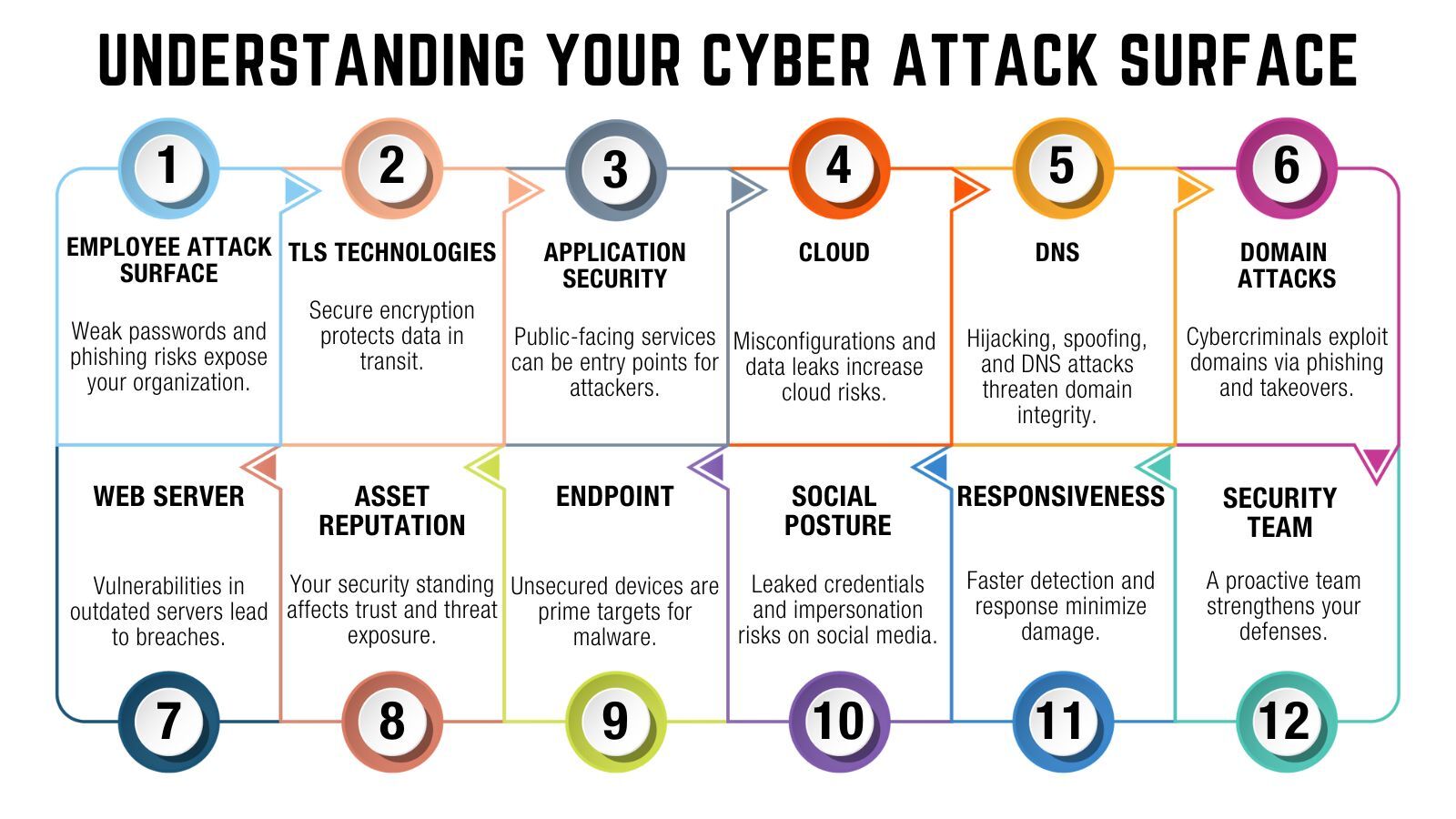
A growing attack surface means businesses must be vigilant in identifying vulnerabilities before attackers do. By systematically evaluating key areas of exposure, you can reduce risks and strengthen security. Here are 12 essential checks to assess and protect your digital assets:
1. Cloud Misconfigurations Unsecured cloud environments are one of the biggest risks organizations face today. Open storage buckets, weak authentication, and excessive permissions can leave sensitive data exposed to cybercriminals. Regular audits of cloud configurations, enforcing least privilege access, and implementing automated security tools help detect and prevent these misconfigurations before they become entry points for attacks.
2. Weak or Compromised Credentials Stolen passwords remain the leading cause of security breaches. Many users still rely on weak or reused passwords, making it easy for attackers to gain unauthorized access. Organizations must enforce strong password policies, implement multi-factor authentication (MFA), and actively monitor for leaked credentials to minimize the risk of credential-based attacks.
3. Unpatched Software and Systems Outdated applications and operating systems often contain known vulnerabilities that hackers exploit. Without timely patches, businesses leave themselves open to ransomware and other cyber threats. A structured patch management process ensures that security updates are applied as soon as they are available, reducing the likelihood of exploitation.
4. Exposed Web Services and APIs Web applications and APIs provide critical business functionality but can also expose sensitive data if not properly secured. Poor authentication, unprotected endpoints, and excessive permissions can create security gaps. Organizations should restrict API access, apply strict authentication controls, and deploy web application firewalls (WAFs) to filter malicious traffic and prevent unauthorized access.
5. Poor Endpoint Security With remote work and mobile devices becoming more common, endpoints are now prime targets for cyberattacks. Unsecured laptops, smartphones, and workstations increase the risk of malware infections and unauthorized access. Deploying endpoint detection and response (EDR) solutions, enforcing encryption, and requiring up-to-date security software on all devices help safeguard endpoints against cyber threats.
6. Insecure DNS and Domain Settings Attackers frequently exploit weak DNS security to redirect traffic, hijack domains, or launch phishing attacks. Without proper protection, businesses risk losing control over their online presence. Enabling DNSSEC, monitoring domain registrations, and using secure domain management services help protect against domain hijacking and unauthorized changes.
7. Shadow IT and Unapproved Applications Employees often use unauthorized cloud services and applications without IT approval, creating security blind spots. These unvetted tools may not meet security standards, leading to potential data leaks and compliance issues. Establishing clear policies, conducting regular IT audits, and restricting access to only approved applications help mitigate the risks associated with shadow IT.
8. Inadequate Network Segmentation A poorly segmented network allows attackers to move freely between systems once they gain access. Without proper controls, a single compromised device can lead to a widespread breach. Implementing network segmentation, applying zero-trust principles, and restricting access between critical systems create additional layers of security, making it harder for attackers to navigate within the network.
9. Lack of 24/7 Threat Monitoring Many organizations struggle to detect security threats in real time, leading to delayed responses and greater damage. Without continuous monitoring, attackers can operate undetected for extended periods. Deploying a Security Information and Event Management (SIEM) system and utilizing Managed Detection and Response (MDR) services provide the visibility and rapid detection needed to respond to threats before they escalate.
10. Phishing and Social Engineering Risks Cybercriminals frequently target employees through phishing emails, fraudulent phone calls, and impersonation tactics. Even with strong technical defenses, human error remains a significant security risk. Regular security awareness training, simulated phishing exercises, and email filtering solutions help employees recognize and avoid social engineering attacks.
11. Insufficient Incident Response Plans A slow or ineffective response to security incidents can turn a minor breach into a major crisis. Many businesses lack well-defined response plans, leaving teams unprepared when an attack occurs. Developing and testing incident response playbooks ensures that employees know how to react swiftly and effectively, minimizing the impact of a security event.
12. Third-Party Security Risks Organizations often rely on third-party vendors and service providers, but these partnerships can introduce new security vulnerabilities. If a vendor's security is weak, attackers may exploit them to gain access to internal systems. Conducting regular security assessments of third-party services, enforcing strict access controls, and requiring compliance with security standards help mitigate these risks.
Reduce Your Attack Surface in 5 Steps
Once you have cleaned up existing vulnerabilities, focus on tightening security protocols to minimize future risks. Follow these five steps to build a stronger defense:
Adopt a Zero-Trust Mindset No one should access company resources without verifying their identity and device security. While it is easier to grant broad access, enforcing strict controls from the start keeps your organization safer.
Strengthen User Access Controls Employees come and go, and their access should change accordingly. Partner with HR to enforce strict password policies and remove access as soon as an employee departs.
Implement Strong Authentication Go beyond basic access controls by layering in role-based or attribute-based access control (RBAC/ABAC) to ensure only authorized users can reach sensitive data.
Secure Your Backups Data backups are a major attack vector. Protect them with strong encryption and strict access controls to prevent unauthorized access.
Segment Your Network The more barriers between an attacker and your core systems, the better. Network segmentation and firewalls help isolate threats, reducing the risk of widespread breaches.
Ongoing Monitoring Is Key Even with these safeguards in place, continuous monitoring is crucial. Regular security assessments ensure vulnerabilities do not go unnoticed. Make security a daily habit, not just a one-time project.
Conclusion
As businesses in Jamaica and across the Caribbean continue to expand their digital infrastructure, the need to secure their growing attack surfaces has never been more critical. With cloud adoption, remote work, and third-party reliance increasing, organizations are more vulnerable than ever to cyberattacks. By proactively managing and securing internal, cloud, and external attack surfaces, businesses can significantly reduce their risk of becoming a target.
The challenges are clear, but the solutions are within reach. By implementing the right strategies, performing regular security audits, and staying ahead of emerging threats, you can protect your organization from the increasing tide of cyber risks. As we have outlined, safeguarding your digital assets requires a multi-faceted approach, but the investment in robust security measures will pay off in the long run.
Is your organization ready to protect its growing attack surface? Do not wait for a breach to strike—partner with Annexus Technologies to fortify your cybersecurity defenses. Contact us today for a comprehensive assessment and a tailored security solution that meets the unique needs of your business.



